時間:2024-01-31|瀏覽:381
1.Discord釣魚
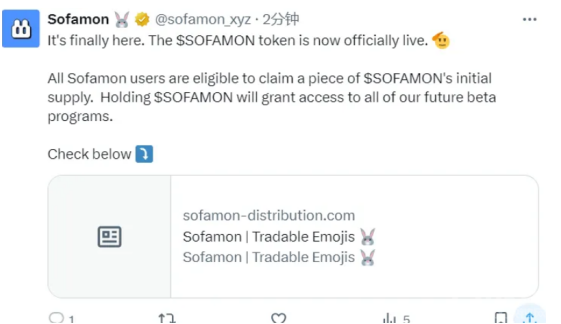
在 Discord 社區中,您可能會遇到類似的消息,聲稱您贏得了獎品,但它們實際上是偽裝的網絡釣魚鏈接。
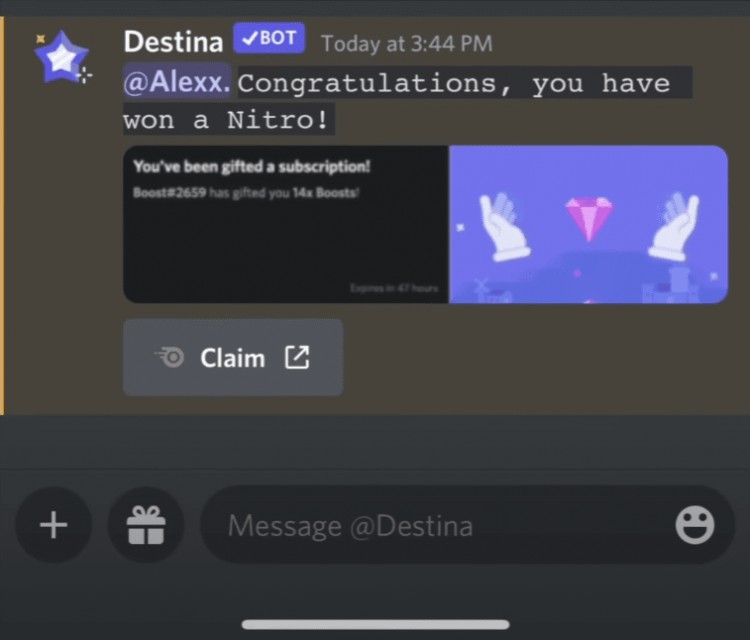
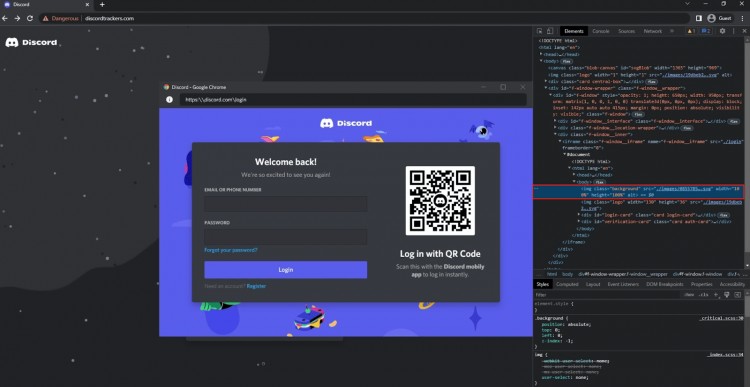
單擊該鏈接將您帶到一個類似于 Discord 的網站,并提示授權。

點擊授權后,會彈出另一個Discord登錄窗口。
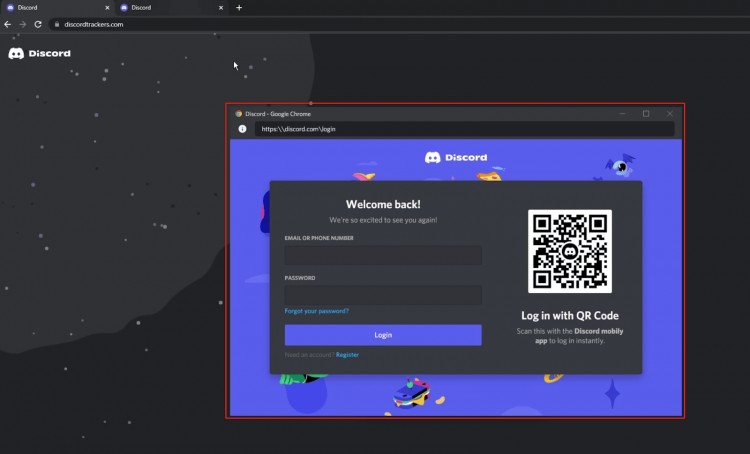
首先,我們無法將該登錄窗口拖到當前瀏覽器窗口之外;
其次,顯示的地址中也有一些可疑的方向。地址「https:\\discord.com\login」使用反斜杠 (\) 進行連接,而官方登錄地址「https://discord.com/login」則使用正斜杠(/)進行導航。
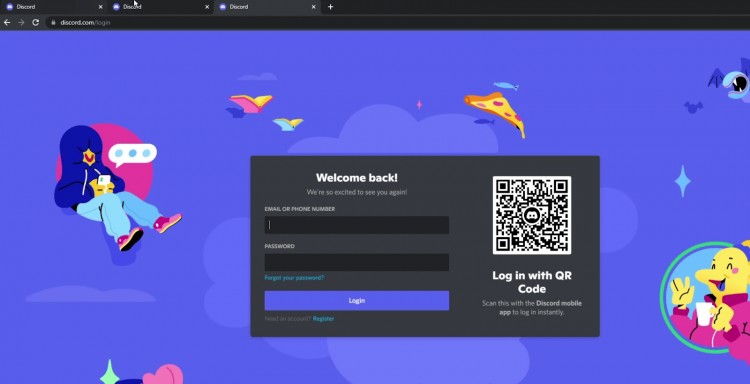
該窗口頁面外觀與非常合法的不和諧登錄窗口縮小,差異縮小。官方登錄窗口圖如下:
一旦在用戶該釣魚頁面輸入賬戶用戶名和密碼,其個人賬戶將立即被泄露,敏感信息將被公開。隨后,欺詐者可以利用這些信息未經授權訪問用戶賬戶并開展欺詐活動。
在瀏覽器開發者模式下檢查網頁源碼
你可以通過瀏覽器開發者模式,檢查網頁源碼。
在上面的釣魚過程中,點擊授權后,彈出的假冒Discord登錄窗口其實不是一個新聞,而是一個嵌入式界面。這是怎么發現的呢?
查看Pages發現,這是一個img源碼標簽,用于在網頁中插入圖片,src用來指定該圖片的路徑。
從官方的Discord登錄窗口進入瀏覽器的開發者模式,如下圖所示:
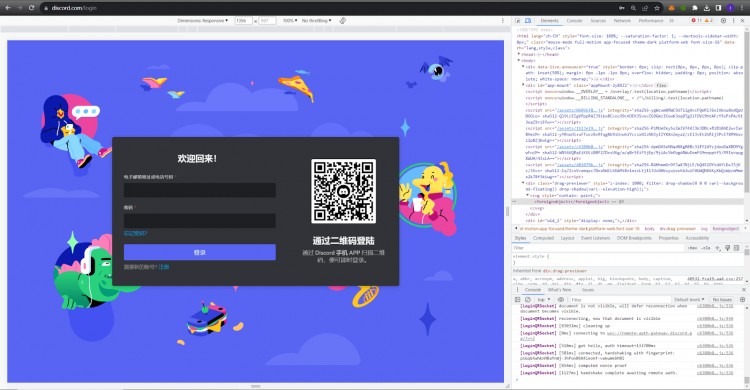
因此,當我們發現異常點之后,可以通過按 F12 進入瀏覽器的開發者模式,查看頁面源碼來判斷我們的懷疑是否正確。尤其是在您點擊外星人鏈接領取獎勵時,更要持懷疑和謹慎的心態進行每一步操作。
2. Twitter釣魚
空投和免費 NFT 是許多人非常感興趣的領域。詐騙者利用被劫持的經過驗證的 Twitter 賬戶發起活動將用戶重定向到網絡釣魚網站。
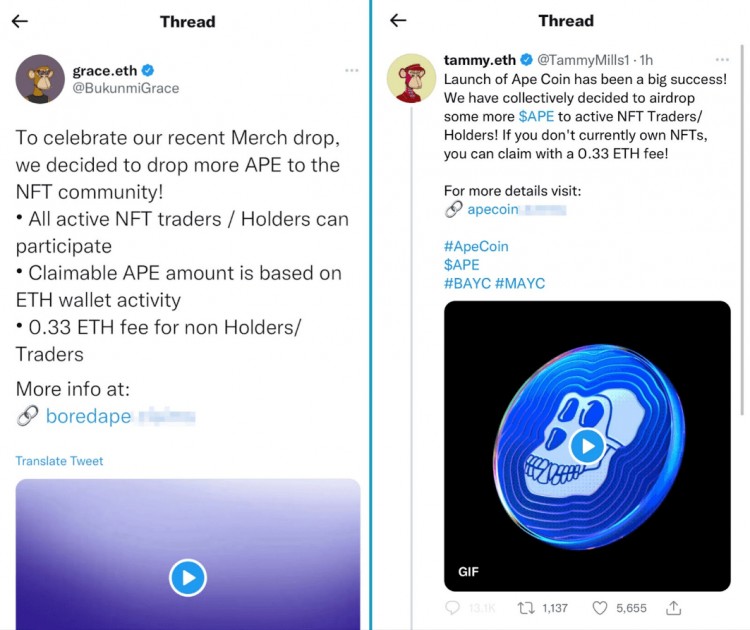
詐騙者利用合法的NFT項目的資產來創建釣魚網站。
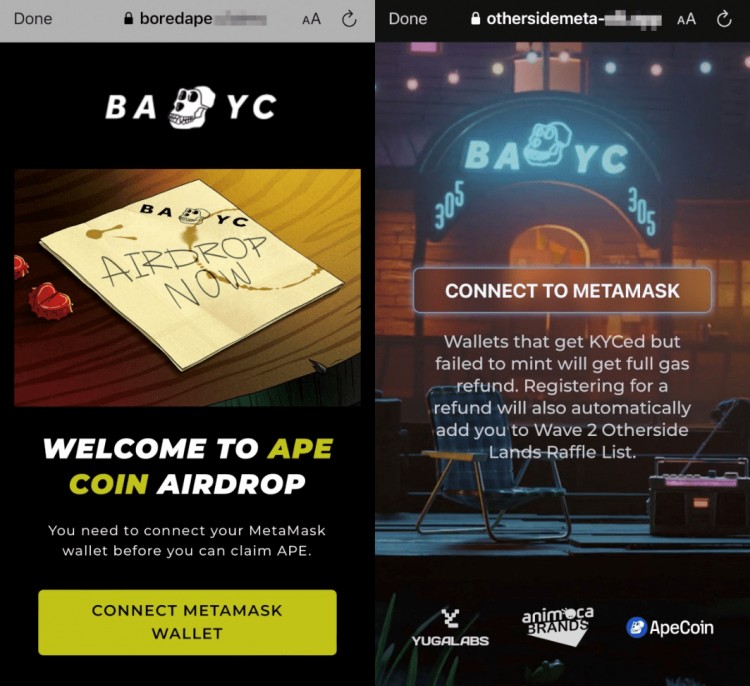
他們利用 Linktree 等流行服務將用戶重定向到編輯 NFT 市場(如 OpenSea 和 Magic Eden)的虛假頁面。

攻擊者將試圖誘使用戶將其加密貨幣錢包(例如 MetaMask 或 Phantom)連接到網絡釣魚網站。毫無戒心的用戶可能會不知不覺地擁有這些網絡釣魚網站訪問其錢包的權限。通過這個過程,詐騙者可以轉出以太坊 ($ETH) 或 Solana ($SOL) 等加密貨幣,以及這些錢包中持有的任何 NFT。
小心 Linktree 中可疑的鏈接
當在用戶 Linktree 或其他類似服務中添加相關鏈接時,需要驗證鏈接的域名。在點擊任何鏈接之前,檢查鏈接的域名是否與真實的 NFT 市場域名匹配。詐騙者可能會使用類似的域名來模仿真實的域名的市場。例如,真實的市場可能是 opensea.io,而虛假的市場可能是 openseea.io 或 opensea.com.co 等。
首選,你找到需要鏈接的官網地址https://opensea.io/,并復制URL。

在Linktree中點擊「添加鏈接」,此時輸入剛才復制的URL,點擊「添加」按鈕。
添加成功,即可在右側看到「Opensea」。點擊「Opensea」,即可重定向到官方的Opensea官方網站。
3.網頁篡改/假冒釣魚
詐騙者發送網絡釣魚電子郵件和鏈接,主題行例如“不要錯過限時 OpenAI DEFI 代幣空投”。該網絡釣魚電子郵件聲稱 GPT-4 現在可供擁有 OpenAI 代幣的人使用。
點擊「開始」按鈕后,您將被重定向到網絡釣魚網站,openai.com-token.info。
將您的錢包連接到網絡釣魚網站。
用戶被引誘點擊「點擊此處領取」按鈕,點擊后,可以選擇使用MetaMask 或 WalletConnect 等流行的加密貨幣錢包進行連接。
連接之后,釣魚網站能夠自動將用戶錢包中的所有加密貨幣代幣或NFT資產轉移到攻擊者的錢包中,從而竊取錢包中的所有資產。
識別真假域名
如果您知道如何識別 URL 中的域名,那么您將能夠有效地避免網頁篡改/假冒釣魚。以下,解釋了域名的關鍵組成部分。
一般常見的網站要么是二級域名,要么是三級域名。
二級由域名主域名和頂級域名組成,比如,google.com。其中「google」是主域名,是域名的核心部分,表示網站的名稱。「.com」是頂級域名,是域名的最后部分,表示域的類別或類型,例如.com、.net、.org等。「.com」表示商業網站。
三級由域名主域名、子域名和域名組成,比如,mail.google.com。「mail」是子域名,「google」是主域名,「.com」是頂級域名。
解釋一下上面的網絡釣魚網站,openai.com-token.info。
「openai」是子域名。
「com-token」是主域名。
「.info」是頂級域名。
很明顯,這個釣魚網站假冒的是OpenAI,OpenAI的官方域名是openai.com。
「openai」是主域名。
「.com」是頂級域名。
How did this phishing website pretend to be OpenAI? The attacker made the first half of the phishing URL look like "openai.com" by using the subdomain "openai" and the main domain ".com-token", where "com-token" uses hyphens.
4. Telegram Phishing
Telegram phishing is a cybersecurity issue worthy of concern. In these attacks, bad actors aim to take control of users' web browsers in order to obtain critical account credentials. To illustrate this more clearly, let's look at an example step by step.
Scammers are sending private messages to users on Telegram with a link to the latest Avatar 2 movie and a straightforward-looking address.
Once you open the link, you'll arrive at a page that looks like a real link to the movie, and you can even watch the video. However, by this time, the hacker had gained control of the user's browser.
Get into the hacker’s shoes and see how they use browser exploits to take control of your browser.
After examining the hackers’ control panel, it became clear that they had access to all information about the browsing users. This includes the user's IP address, cookies, proxy time zone, etc.
Hackers have the ability to switch to the Google Mail phishing interface and perform phishing attacks against Gmail users.
At this point, the front-end interface changes to the Google Mail login page. The user enters their account credentials and clicks the login button.
In the background, the hacker successfully received the login username and password. This method is used to maliciously obtain user account and password information, which ultimately leads to leakage of user information and economic losses.
Check the remotely loaded JavaScript script in the web page source code
You can enter the browser developer mode and check whether there are remotely loaded JavaScript scripts in the source code of the web page. This script is the key for the attacker to control the user's browser. How to determine whether there is such a phishing script in the link you click?
In the above phishing process, you enter the link to the "Avatar 2" movie. You can press the F12 key to enter the developer mode of the browser and find that the link points to a remotely loaded JavaScript script. Hackers remotely control the browser by executing script content to obtain the user's account and password.
While watching the "Avatar 2" movie on a regular website, we entered the developer mode of the browser and did not find any JavaScript scripts pointing to remote loading.
5. Metamask fishing
Here, taking the Metamask plug-in as an example, we will introduce how an attacker can use this plug-in to steal the user's wallet private key.
The attacker obtains the target user's contact information, such as email address or social media account. Attackers pretend to be trusted entities, such as the official Metamask team or partners, and send phishing emails or social media messages to target users. Users receive an email impersonating MetaMask, asking to verify their wallet:
The user clicks "Verify your wallet" and enters the following page, which claims to be Metamask's official website or login page. During the actual phishing attack, we found two different phishing pages. The first directly asked the user to enter the key, and the second asked the user to enter the recovery phrase. The essence of both is to obtain the user's metamask key.
The attacker obtains the victim's private key or recovery phrase and can use this information to access and control the target user's Metamask wallet and profit by transferring or stealing the target user's cryptocurrency.
Check Metamask email and domain
If you need to install the Metamask plug-in on chrome, the official link is https://metamask.io/
A link that contains phishing scams is https://metamaskpro.metamaskglobal.top/#/, please pay attention to screening.
When you receive an email from a suspected Metamask, you need to pay attention to identify the sender and recipient information:
There are serious misspellings in the sender's name and email address: Metamaks instead of MetaMask.?
The recipient does not include your real name, some other information that identifies you, and a clearer description of what needs to be done. This proves that this email may be sent in bulk and not just to you.
Secondly, you can also check the authenticity of these links by domain name:
Click "Verify your wallet" to enter the phishing webpage, metamask.authorize-web.org. Analyze this domain name:
"metamask" is a subdomain
"authorize-web" is the main domain name
".org" is the top-level domain name
If you know the official domain name of metamask, metamask.io, you will easily find that you have been attacked by a phishing attack:
"metamask" is the main domain name
".io" is the top-level domain name
The phishing site's domain name, metamask.authorize-web.org, has an SSL certificate, which tricks users into thinking it's a safe place to trade. But you need to note that the use of MetaMask is only under the subdomain name of the registered top-level domain.
6. VPN Phishing
A VPN is an encryption technology used to protect the identity and traffic of Internet users. It encrypts and transmits user data by establishing a secure tunnel between the user and the Internet, making it difficult for third parties to invade and steal data. However, many VPNs are phishing VPNs, such as PandaVPN, letsvpn, and LightyearVPN to name a few. Phishing VPNs typically leak the user’s IP address.
When you connect using a VPN, your device sends a DNS request to the VPN server to get the IP address of the website you want to visit. Ideally, a VPN should handle these DNS requests and send them through the VPN tunnel to the VPN server, thus hiding your true IP address. If you are using a phishing VPN, a DNS leak can occur and your real IP address may be recorded in DNS query logs, making your online activities and access records traceable. This can destroy your privacy and anonymity, especially if you are trying to hide your real IP address.
IP leak self-check
When you use a VPN to surf the Internet, you can test whether the VPN is leaking your IP address through the ipleak.net or ip8.com websites. These websites can only display your public IP address, which is the IP address assigned to your Internet connection. If you are using a VPN service, these websites will display the IP address of the VPN server you are connected to, rather than your real IP address. This can help you verify whether the VPN is successfully hiding your real IP address.
You can check if your IP address has been compromised by following the instructions below:
Open your browser and visit ipleak.net, which will display your current IP address. As shown in the image below, your IP address appears as 114.45.209.20. And pointed out that "If you are using a proxy, it’s a transparent proxy." This indicates that your IP address has not been leaked and that your VPN connection is successfully hiding your real IP address.
這時,你也可以通過 ipconfig /all 命令行查詢你的真實 IP 地址,如果這里查詢的 IP 地址和通過 ipleak.net 查詢的 IP 地址不一致,則表明你的 IP 地址確實被隱藏了。如果一致,則表明你的IP暴露了。如下圖所示,通過ipconfig /all查詢機本真實IP地址為192.168.*.*,與上圖所示的114.45.209.20不一致,IP地址未泄露。
總結
綜上所述,我們詳細介紹了六種 Web3 社交工程攻擊方式,并提供了相應的識別和預防措施。為了有效避免 Web3 社交工程攻擊,您需要提高對陌生人鏈接、郵件以及來自社交平臺的消息的除此以外,我們還建議您了解如何在瀏覽器的開發者模式下檢查網頁源碼,如何識別真假域名,如何自檢IP地址是否泄露,并分析其中存在的安全隱患。
熱點:WEB